How to Secure VPN Access for Your Teleworkers

Very few organizations were fully prepared for the amount of remote work that is now mandated across the United States. As companies are still troubleshooting their teleworking systems and processes, they may be open to security threats. As the Department of Homeland Security’s (DHS) Cybersecurity & Infrastructure Security Agency (CISA) recently warned, there are specific cyber vulnerabilities that arise from working at home. One major threat comes from employees using a virtual private network (VPN) to remotely access secure company materials.
Connecting to a VPN is a best practice for cybersecurity, but hackers are diligently targeting vulnerabilities. VPNs are running 24/7, which means that organizations are less likely to make sure they have the latest security updates and patches. It should come as no surprise then that hackers are using this opportunity to target unpatched VPNs.
Secure VPN Access
All organizations should be extra vigilant in their cybersecurity. There are a few areas where organizations can adopt a heightened security lens:
Users
Understand who has access and to what information. Be sure to segment your users and make sure you are using multi-factor authentication to authenticate them.
Identify and label any sensitive data and ensure that only the appropriate people can access this. Many organizations do not currently have their data classified, but this can be done very efficiently with software from vendors like Varonis.
Review corporate policy and segmentation within your organization. Segmentation is an effective security tool to prevent intruders from accessing an internal network. Microsegmentation allows you to quickly separate your network into hundreds or thousands of protected microsegments. Unisys Stealth and VMware NSX are excellent platforms for microsegmentation and isolation.
Use Multi-Factor Authentication (MFA) for remote access. Implementing MFA on all VPN connections will increase security and can make you less susceptible to phishing attacks. Some vendors we recommend and install at ivision are Okta, Duo, or Microsoft Azure MFA.
Endpoints
Think ahead about your endpoints. Know how you’ll handle threats posed by data leakage, or from devices on your network. We recommend a mix of Security as a Service (SOCaaS), encryption, and isolating all the way to the endpoint.
Prepare employees for phishing attempts. You should have something in place to make sure employees can easily report phishing emails. Malicious actors are taking advantage of employees working from home, so invest in a phishing protecting software from a company like Microsoft, Ironscales or KnowBe4.
Prepare your IT team to ramp up security tasks. Security personnel should be ready to scale log review, attack detection, and incident response and recovery. This is another time where a SOCaaS is beneficial.
Tried and Tested Network
Stress test your infrastructure. It should be robust and able to handle a large volume of traffic. Many organizations have this infrastructure implemented, but it is critical that you also test it.
Update everything with the latest software patches and security configurations. This includes VPNs, network infrastructure devices, and devices being used to remote into work environments. As hackers are targeting vulnerabilities, it’s absolutely critical that your VPN is continually updated.
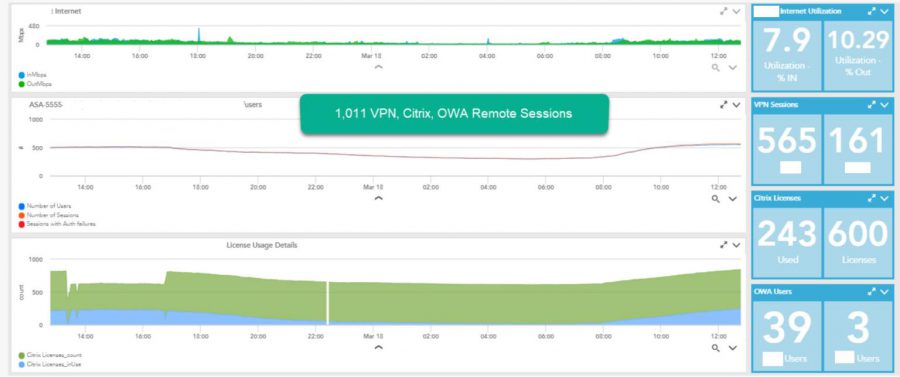
Know your VPN limitations. Ensure that you are prepared for large amounts of users accessing VPN. Make sure that you can prioritize users who require higher bandwidths as well. Below is an example of a dashboard we use to monitor and test for an ivision client.
Let us know if there are any challenges within your organization that require assistance. We are here to help keep your systems running smoothly and securely during this unprecedented time.