Understanding Microsoft’s Enterprise Mobility + Security

As cyberthreats grow more sophisticated, on-premise solutions cannot effectively protect sensitive data. Enterprise Mobility + Security (EMS) provides one control panel in the cloud for identity management, device management, information protection and secure access to apps and resources. You don’t have to trade mobile flexibility for enterprise security — a mentality of adoption, adaptation and scalability will ultimately help restructure your posture for a comprehensive approach to promote a proactive EMS solution.
Utilizing EMS and its intelligent set of tools that are integrated with Azure and Office 365’s platforms provide you with a conclusive path to improve your cloud and hybrid security postures. It’s also a great tool for environments that want to better control their assets and intellectual property (IP), while minimizing the impact of human resources needed. Whether your business embraces a Bring Your Own Device (BYOD) or Choose Your Own Device (CYOD) program, cloud applications, Office 365 and Microsoft Intune work together to improve all of your security controls for Microsoft Office 365.
In this series about Microsoft’s EMS, we will provide you with an overview of the platform, its primary features followed by real-world examples tied to its abilities and how to understand where they add value to your environment with an extreme focus of protecting your end-users as well as corporate data.

Let’s review how these tools improve security posture
Securing productivity, collaboration and enterprise data is critically important as organizations digitally transform. EMS aids management functionalities over workstations, laptops, tablets, smartphones and apps with less on-prem resources paired with its ability to balance workloads with SCCM/ConfigMgr integration.
To help associate security concepts in this deep-dive, Microsoft breaks down the features to a more digestible form of platform pillars as shown below from which we’ll explain their roles and coverages accordingly.
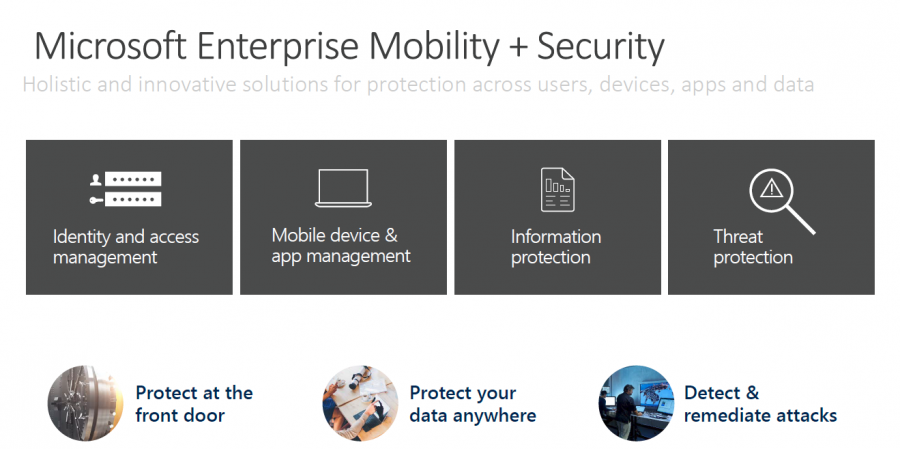
Protecting Your “Front Door”
A solution starts with identity protection capabilities to secure access at the “front door” of your company’s apps and data. Azure Active Directory Identity Protection leverages billions of signals to provide risk-based conditional access to your applications and critical company data, including the option of multi-factor authentication.
By calculating risk severity for every user and sign-in attempt, risk and conditional-based access rules can be applied to protect against suspicious logins. Sign in once for secure access to all corporate resources, on-premises and in the cloud, from any device. This includes pre-integrated support for Office365 and thousands more popular SaaS apps.
Microsoft also helps you manage and protect privileged accounts with Azure Active Directory Privileged Identity Management so you can discover, restrict and monitor privileged identities and their access to resources.
Protecting Your Data & Identities Anywhere
Microsoft provides deep visibility into user and data activity, so you can protect your company when users make poor choices as they work with critical company data. Gain deeper visibility into user, device and data activity on-premises and in the cloud to create more effective, granular level policies. Classify and label file at creation, track their usage and change permissions when necessary.
Microsoft Cloud App Security provides visibility and controls for cloud apps, including popular SaaS apps like Box, Salesforce, ServiceNow and of course, Office 365. With the new Azure Information Protection, Microsoft brings together classification and labeling with persistent data protection to enable secure file sharing, internally and externally.
Finally, Microsoft IntuneMobile App Management (MAM) helps you prevent data loss on devices with the unique ability to manage the Office mobile apps with or without requiring device enrollment.
Detecting & Remediating Risks Before They Damage
As more organizations move to an assume breach posture, Microsoft’s EMS Advanced Threat Protection (ATP) identifies attackers in your organization using innovative behavioral analytics and anomaly detection technologies―on-premises with Microsoft Advanced Threat Analytics and in the cloud with Azure Active Directory and Cloud App Security.
Threat intelligence is enhanced with the Microsoft Intelligent Security Graph driven by vast datasets and machine learning in the cloud. Identify attackers in your organization using innovative behavioral analytics and anomaly detection technologies – all driven by vast amounts of Microsoft threat intelligence and security research data.
With Information Rights and Protection, you’re able to enable users to protect and control data. Employees can encrypt virtually any type of file, set granular permissions and track usage. The encryption stays with the file where it goes, enabling more secure file sharing, internally and externally.
Expand Your Security with EMS

All things considered, today’s tools with Microsoft Enterprise Mobility + Security allow enterprises greater protection, detection and response capabilities for your mobile workforce. EMS and its products increase the security features of Windows 10 and Office 365 while extending them further into your entire environment including third-party investments and promote a single point of Enterprise Mobility Management.
Next time we’ll take a deep-dive in how to integrate your on-prem SCCM with Microsoft’s Intune for a balanced workload on device management.



