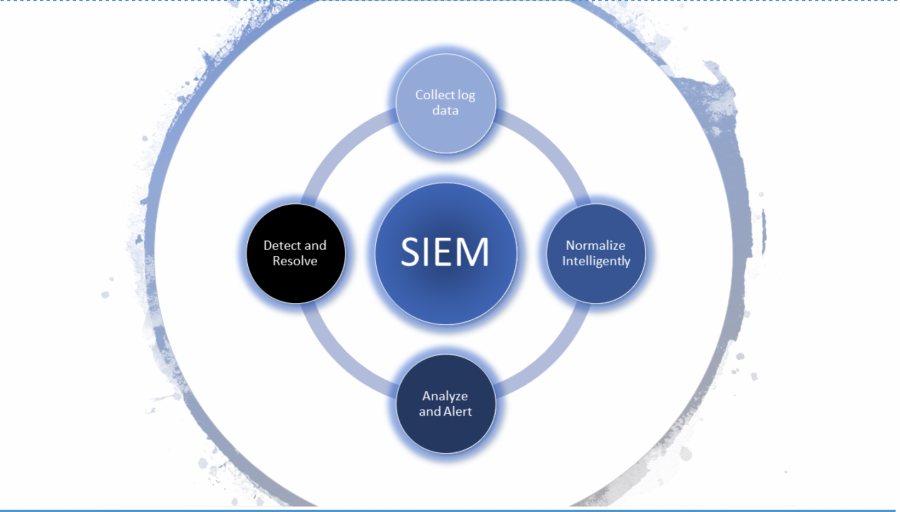
SIEM Capabilities: Monitoring and Detecting Potential Risks

If you’ve spent any time paying attention to security technology, you will undoubtedly have heard the term “SIEM,” or Security Information and Event Management. For a time, this term was used to refer to simple centralized log aggregation and monitoring, but SIEM products have matured alongside technology advances. SIEM now includes detailed log analysis and correlation, incident reporting, risk management, behavioral threat detection and actionable analytics, and each of these functions directly supports the ongoing detection and response to security incidents in an organization.
Log Aggregation and SIEM
Log aggregation is typically the first feature that leads an organization to start thinking about implementing a SIEM to support their security requirements. You can’t understand or monitor what you aren’t collecting, and it’s commonly accepted that even the absolute best technologies can’t prevent 100% of potential risks. Additionally, certain certifications or accreditations require that logs be aggregated and stored for audit purposes. While log aggregation can be an important part of certification compliancy, it can also provide far greater value to an organization if leveraged as part of a larger overarching SIEM program.
A SIEM system works by capturing—by way of log aggregation—the forensic information required to uncover security incidents or breaches and escalating them to a Security Operations Center (SOC) for review and remediation. In many cases, the logs stored in a SIEM will be the difference between a detected breach and an undetected breach–that is, if the SIEM program and process can review the logs and react in an appropriate timeframe.
The Benefits of SIEM
Early log aggregation and alerting platforms focused on an alert-heavy signature-based model, which inundated SOC analysts with false-positive alerts or heavily manual correlation of events. As a result, many organizations struggled to see a return on the investment of these platforms.
To address this deficiency, SIEM products began implementing more intelligent event correlation processes, allowing sources to be aggregated and reviewed programmatically, detecting relevant patterns and abnormal behavior with far more speed and efficiency than a security analyst could. This then allows the SOC analysts to review more insightful data and detect threats much earlier and with less overhead. As these technologies have matured, they’ve reached a point where even extremely complex incidents can be uncovered quickly, minimizing the potential for damage.
The Challenges of SIEM
Even with technology advancements, the interconnected nature of the SIEM in an environment, the complexity of most organizations’ infrastructure and the difficulty in generating clear end-state requirements can make the implementation of a SIEM challenging. A SIEM is only as effective as the information it alerts on, so properly defining the data sources, correlation goals, and appropriately reviewing and tuning over time are paramount to its success. Once that is complete, a consistent deployment and the addition of SIEM into your deployment lifecycle works to prevent gaps from appearing as the environment changes. Each of these steps in the process take time and labor, so it’s important to forecast the necessary resources to determine whether the existing staff has the availability to successfully implement and manage internally or whether it makes more sense for your organization to offload those responsibilities to a directly focused team as a managed service.
As infrastructure becomes increasingly complex and more people are moving to a hybrid IT environment between on-premises and cloud deployments, there is a greater need for a centralized SIEM presented through a single interface. Each of these infrastructure components adds a layer of complexity and has the capability to introduce additional vulnerabilities in the configuration or code. When implementing a SIEM, it is important to ensure that it meets the needs of your organization and that you have a clear plan that directs on how to return value from the implementation.
At ivision, we are passionate about helping our clients return security value from a SIEM. We are happy to help your organization determine how best to implement security technologies to help keep your information secure.