Reputation Risk Management and Cybersecurity

One of the biggest current threats to an organization’s reputation is data breaches. Companies are expected to protect their clients’ personal data – so a security incident can affect public sentiment for an organization. This wave of negativity and reputational loss can lead to customers severing their connection to the company. Not only that, but a brand’s reputation impacts whether or not they can attract the best talent or suppliers and affects their business partnerships. A successful cyberattack, then, directly impacts the bottom line.
Background on Cybersecurity Risks
As more companies migrate their infrastructure to cloud-based systems, the threat of a cybersecurity incident grows. Many companies rely on aging network infrastructure and processes or run outdated, vulnerable software. A recent CEO and Board Risk Management report by Deloitte surveyed 400 CEOs and board members on how they prioritize investments for specific risk areas. Of those 400, 41% cited “security, including physical and cyber breaches” as the greatest threat to their reputation.
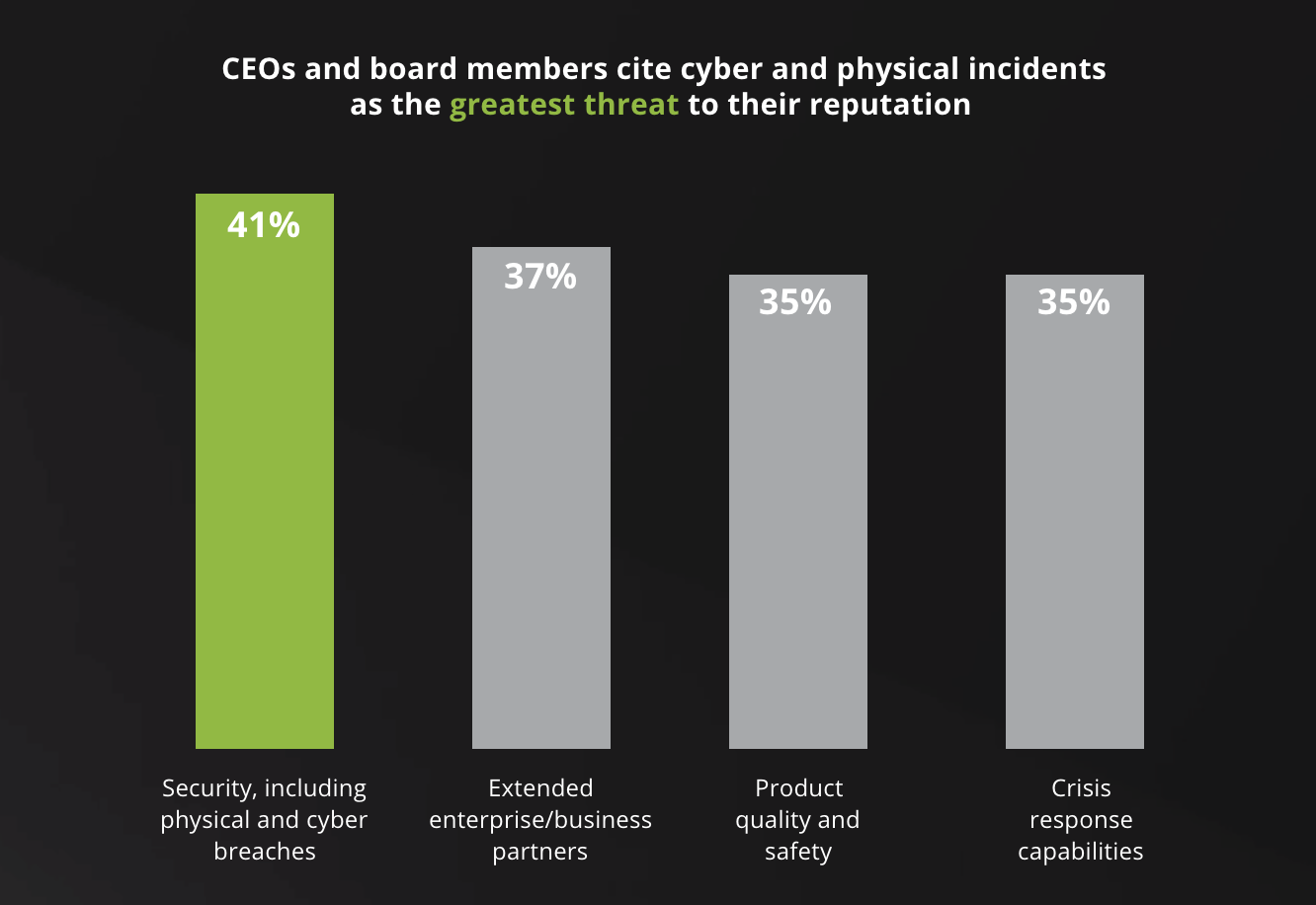
Source: CEO and Board Risk Management Report, Deloitte
Many cybersecurity programs focus on the traditional perspective of investing in prevention technologies. However, the Internet of Things (IoT) and artificial intelligence (AI) pose a huge risk to organizations. Even companies that have implemented business continuity and disaster recovery plans are not necessarily resilient against evolving threats. Also, many business leaders are often misaligned about cybersecurity, and are unsure of where to invest for IT. As shown below, a concern for cybersecurity does not translate into an executive commitment to its risk management.
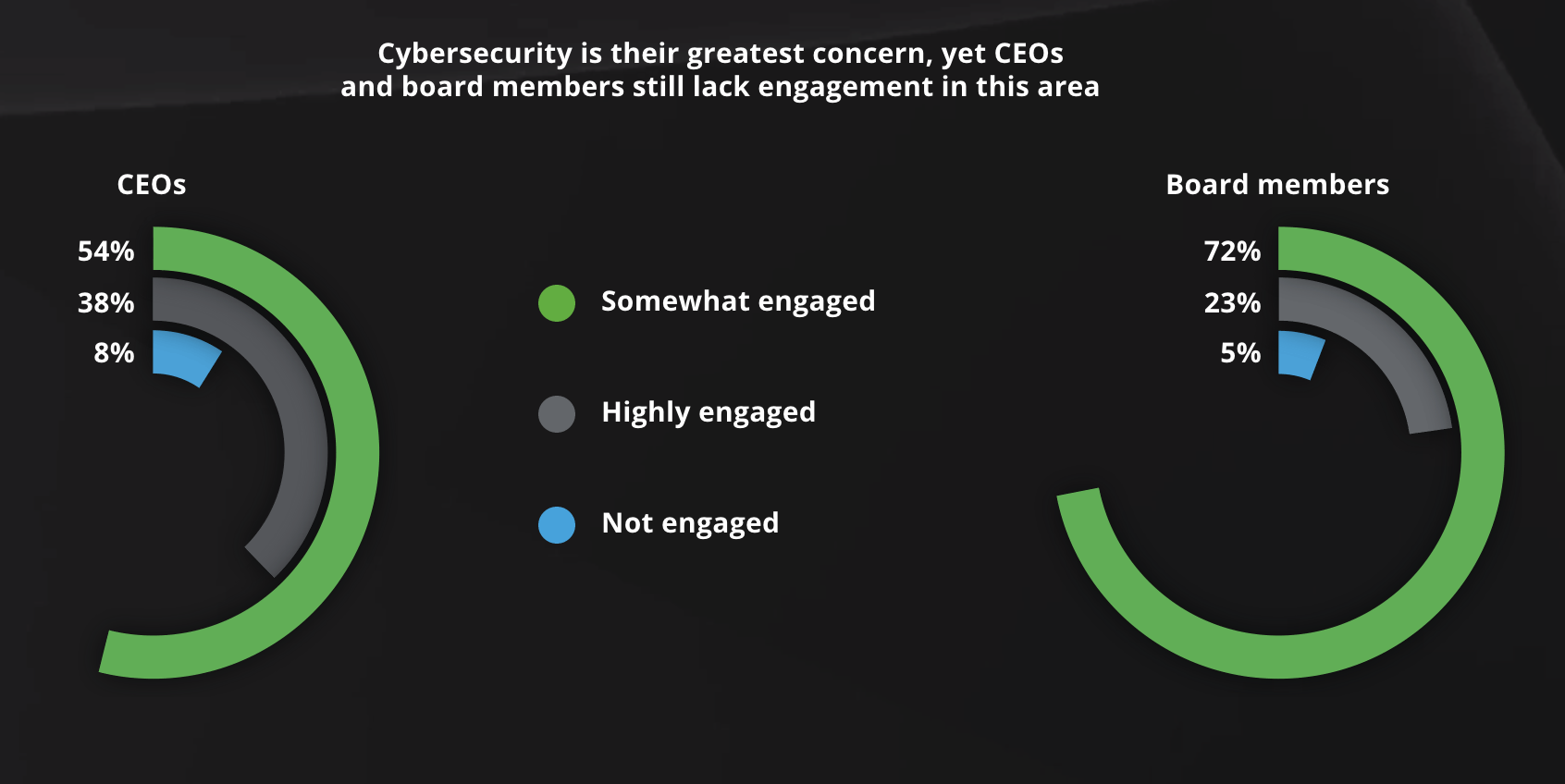
Source: CEO and Board Risk Management Report, Deloitte
Why Reputation Risk Management Matters
While building a reputation can take years, tarnishing a reputation is as easy as one security breach. It is strategically valuable for companies to demonstrate transparency and build public trust. Customers are more aware than ever of potential risks to their personal data, and they are more aware of what protections they are owed from companies.
“It takes 20 years to build a reputation and five minutes to ruin it.” – Warren Buffett
GDPR and Consumer Awareness
The General Data Protection Regulation (GDPR) has had a global impact on public awareness for personal data protection. Since it went into effect in 2018, GDPR has placed signification obligations on companies to stay compliant. It has also ensured that EU citizens will be notified of any breach to their personal information. Those consumers are able to access their own data more easily and can understand how their data is being used.
GDPR has also inspired other countries around the world to introduce legislation concerning personal data. Because the public is becoming increasingly more knowledgeable about data protection, companies must acknowledge that a data breach can have a significant impact on their reputation.
The Real Costs of a Data Breach
A 2018 study by Ponemon Institute found that the average cost of a data breach is $3.86 million. Of this number, the indirect costs from reputation loss frequently outweigh the direct costs of fines or legal battles. For larger attacks involving 1 million to 50 million records, the costs can be extraordinary. A data breach of that size can cost between $29 million to more than $400 million – and that doesn’t include costs incurred from a damaged reputation. This can include expenses from addressing the problem and notifying customers, as well as the cost of lost sales and brand damage.
Organizations that work proactively to build customer trust, both before and after a breach, are better protected against reputational damage. Cyber risk and reputation management strategies should therefore go hand in hand. Corporate executives tend to focus on priorities that they see as making a big difference to the company, and cybersecurity tends to get little attention. It’s no surprise, then, that companies spend on average only 3.3% of their revenue on IT, with only a fraction of that being allocated for cybersecurity.
Getting Ahead of Cybersecurity Incidents
For cyberattacks, it is not a matter of if but when for a company. For companies that hold particularly sensitive information – such as organizations in the financial, healthcare or legal industries – cybersecurity should be a top priority. If your business is built on trust, then reputation management is critical. By implementing a few key processes to bolster security, any organization can mitigate loss from a security breach.
First, make sure that your company has an actionable plan in place. This includes both a strong cybersecurity framework and crisis management tools, such as formal response plans for timely public outreach. Having a strong security posture will reduce your exposure to risk, but a crisis management plan should still be put in place to mitigate any reputational harm.
How to mitigate reputational risk:
- Identify risks through a stakeholder lens
- When it comes to identifying the reputational impact of potential risks, consider your customers’ perspectives. Why do they trust your company? What would they consider to be an unforgivable breach of that trust? Prior to a crisis, your management teams should meet to think through potential issues. It’s important to identify future risks before they happen.
- Encourage cross-departmental collaboration
- One of the biggest challenges for any company is organizational silos. In other words, employees (or even entire departments) do not have the ability to share important knowledge with one another. Silos are like barriers to change and communication and can make it difficult to collaborate when critical problems arise. When communication thrives, it’s easier to identify and tackle emerging threats.
- Prioritize reputational risk as a business strategy
- It’s often hard for IT leaders to determine the appropriate areas on which to spend their limited budget. Many times, there is a struggle to translate IT risks into a language that non-technical executive leadership and board members can understand. However, a reputational risk management strategy should be a security priority for any organization, and executive buy-in is key for success. You should work to implement a strategic plan that anticipates reputational impacts, rather than just being reactive to a damaging event.
- Establish a risk governance structure
- The executive team plays an important role not only in supporting a strategy, but also in doing damage control. The CEO and other C-suite executives play a critical role in setting the tone after an event occurs. When setting a crisis management strategy, your organization should work collaboratively to select leadership representatives across all business units. The best way to manage misinformation is to designate individuals who are the only people authorized to serve as the voice of a company in times of crisis.
- Formalize and practice
- Once you formalize all the essential aspects of your crisis plan – how to mobilize a response, make decisions and what information to communicate – it’s time to practice. Run simulation rehearsals based on a few critical reputational risks. Make sure that all the major players know their responsibilities in the event of a reputation-damaging cybersecurity incident.
Responding to an Attack
- Recognize reputational risk early
- Just like you should have eyes on your IT systems at all times, you should also have employees monitoring your reputation. This is central for identifying emerging reputational threats. Not every cybersecurity incident will damage your company’s brand – but always keep tabs on how customers are responding regardless. In the digital age, this means performing 24/7 monitoring of social media.
- Execute the plan
- You have a plan and now it’s time to execute it. During a crisis, there are usually two priorities running parallel to one another: containing and resolving the incident and addressing both short- and long-term risks to your reputation. Be sure to have responsive communications and a consistent narrative if you want to maintain customer trust.
- Follow through
- If you make a public commitment, deliver on it. Rebuilding trust might take a long time after a data breach but maintaining promises is critical. A failure to effectively manage a crisis can be devastating for your long-term reputation.
Business Resilience
Technology is evolving at a pace that far outpaces security protections. With the demands of a global economy, businesses are expected to maintain continuous operations. Third-party managed services providers offer services like Backup as a Service (BaaS) and Disaster Recovery as a Service (DRaaS) to ensure data protection. However, business continuity and disaster recovery protections only represent half of your overall business resilience – or ability to rapidly identify and respond to disruptions. Data loss can halt business operations and create significant financial loss, but it can also have a damaging effect to your reputation and result in even more long-term cost.
Think about large organizations that experienced well-publicized breaches over the past few years. For many of those, the public didn’t find out about a breach under long after it occurred. We live in an interconnected world where information of a cyberattack can spread online within minutes. Hiding an event will only create more reputational damage when it is revealed later on. A proactive reputation risk management plan integrated with your cybersecurity strategy will go a long way in creating a truly resilient business.



