Load Microsoft Authenticator on your PC for MFA
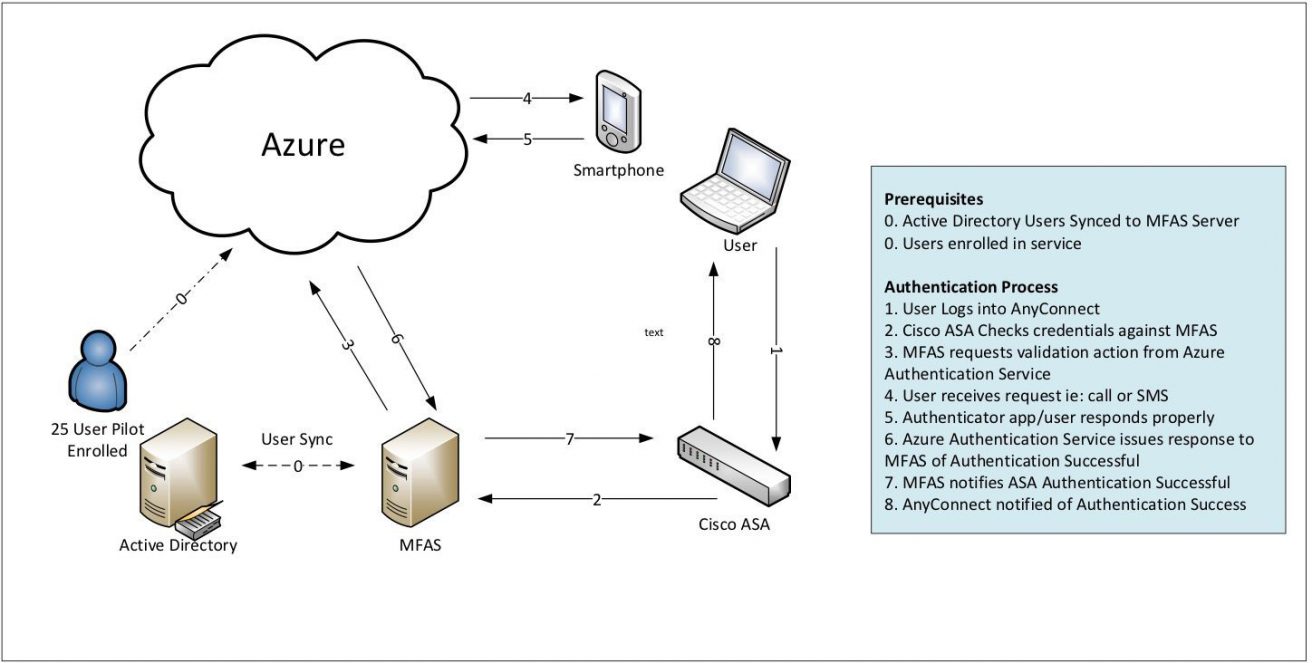
I was working with a client recently who wanted to take advantage of Microsoft Azure’s Multi-Factor Authentication (MFA) service. This service can do a great number of things, but in particular, they wanted to be able to integrate into MFA with their Cisco ASA VPN solution in order to help with PCI compliance.
Setting up Microsoft Azure’s multi-factor authentication service
This design involves setting up an MFAS server onsite and then integrating it via RADIUS to be part of the Authentication chain. The service is pretty robust and most clients would choose to use their phone to receive the phone call, text message or even run the Authenticator App from Microsoft (Android, iPhone, and Windows Stores) in order to provide that second factor in the authentication process.
This is all pretty straight forward. The challenge with this client is they needed to support the use case of having users in different parts of the world who cannot be guaranteed of having access to a phone. This would then mean they would have to fall back to issuing physical “hard token” device. Since the service is based on standards any OATHO token using TOTP (time-based one-time passwords) would work. However, Microsoft has tested a few of these such as Gemalto IDProve, Deepnet Security Safeld and Safenet OATH tokens which are the ones I would suggest you start out with. The problem was if they went down this path they would have a whole new set of problems to think about. Namely, how to manage global distribution and management of these new physical assets moving around the globe.
Leveraging Microsoft’s Authenticator
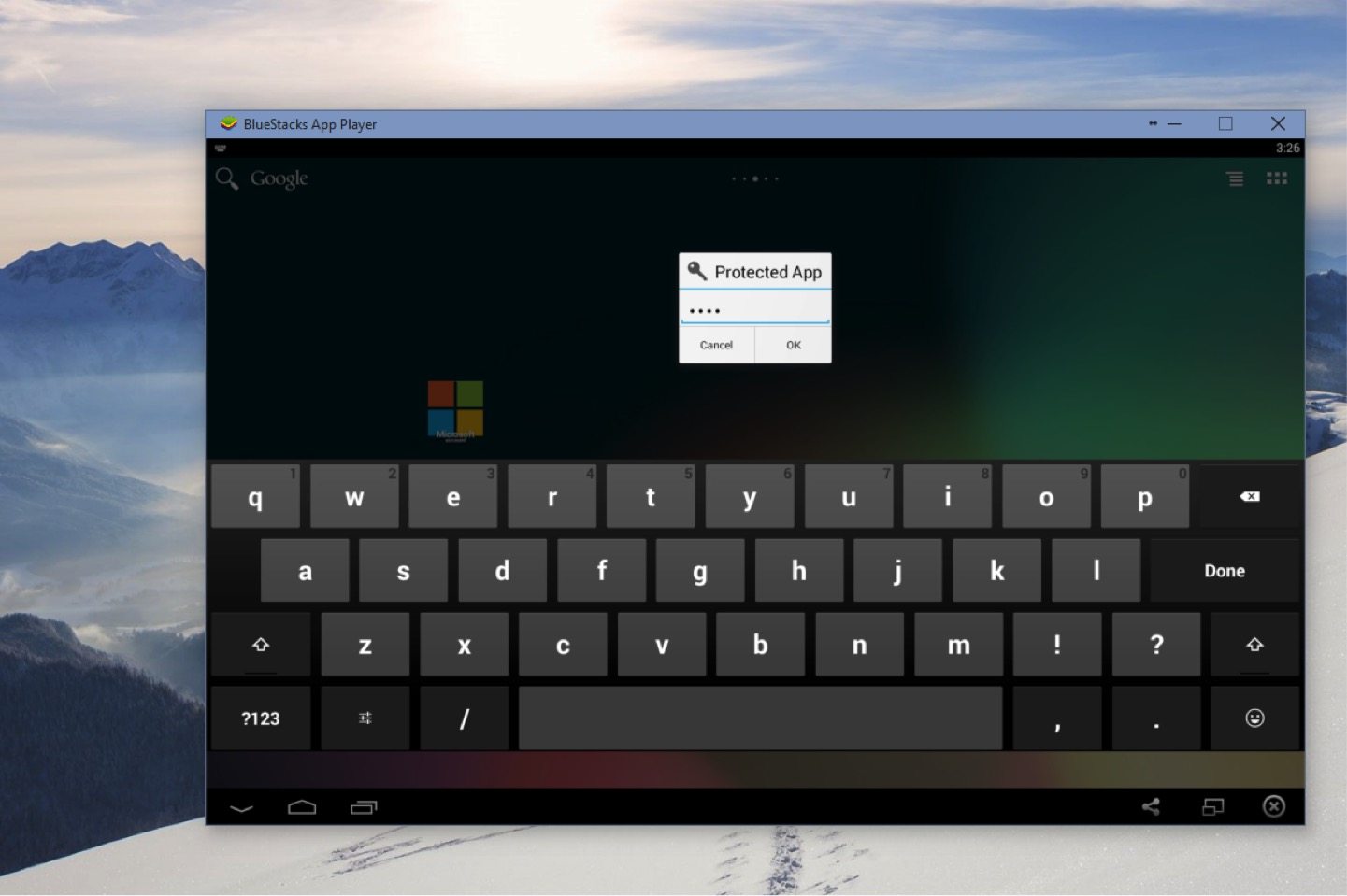
A potential solution came up which is a little outside of the box, but has some promise. Leveraging Microsoft’s Authenticator App on the PC itself. To do this I installed a device emulator for Android on my PC. This emulator acts just like a typical Android device, and since it allows me to install applications from the Android Marketplace I could also install Microsoft’s Authenticator Application. I then enabled a PIN on open for the application for some added security.
Now when the user needs to VPN in they can run the same Authenticator which runs on an Android Phone on their PC. With this, they can provide the ever-changing security code and gain access to their environment.
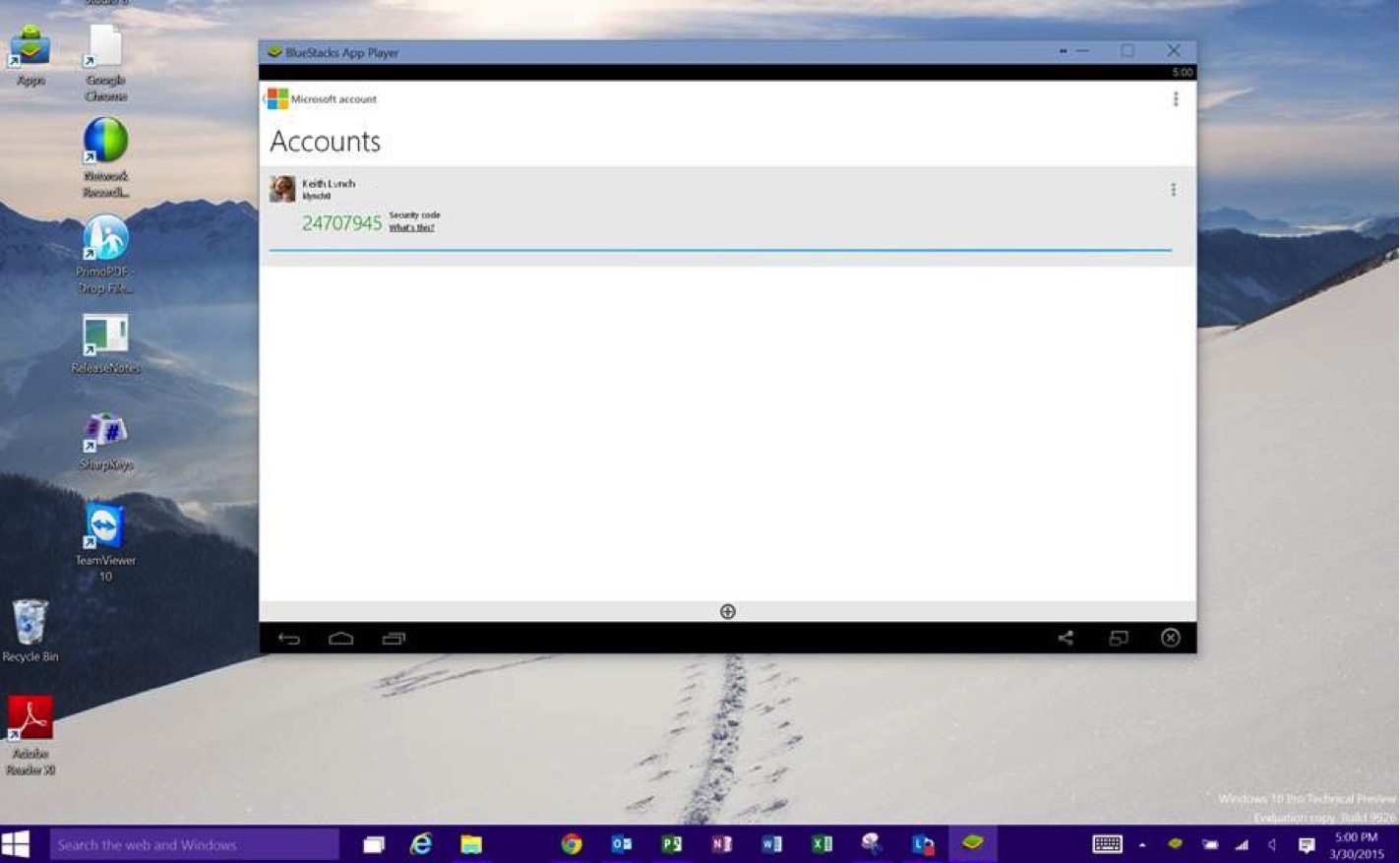
I realize this breaks the whole “something you have and something you know” as the application sits on the PC that is VPN’ing in. But sometimes a custom solution is required.



