Security Awareness Training: Secure Your Company Culture

Every day it seems like there is another security incident or attack that has critically impacted the targeted organization. In a large number of these, the attack directly involved the organization’s own employees or users. For example, a recent coordinated ransomware attack hit the computer systems of local government agencies in 22 small Texas towns. Ransomware attacks like this one often begin after an employee clicks through a link or downloads an attachment in an email.
Email security continues to be a top threat for companies of all sizes and sectors. The Texas incident is an important reminder that all organizations can benefit from a culture of security awareness. Respondents in the Cisco 2019 CISO Benchmark Study confirmed that email security issues comprised two of the top three most common types of security incidents:
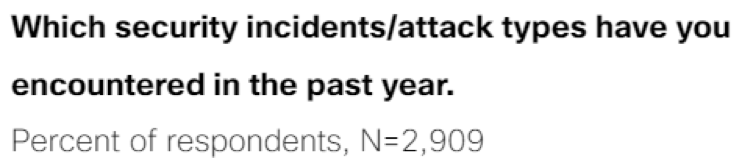
Security awareness training is a routine part of the information security playbook for many organizations. Most companies provide their user community with the general training required to check the box in an audit. Few fully integrate this mindset into their culture. It is critical that companies do more than provide basic training on security awareness. Employees should be both trained on and tested for their understanding of targeted security threats. Companies must assess if their training is actually creating a security-focused culture.
Assessing your security awareness training
It is important to routinely assess your company’s security awareness training program. An easy way to do this is by asking yourself some of the questions below:
- Does your training program include accountability across all organizational levels for those who do not complete the required training?
- Do you validate user understanding by frequently testing employees with automated tests, social engineering engagements or other exercises?
- Do you use metrics to measure both compliance with your training and validation exercises, and the impact on real-world attacks? How do these metrics influence changes to your program?
- Does your organization understand the importance of your security awareness training? Or does the user community treat the training due date as a roadblock?
- Does your organization share the wins related to the metrics that you track? Does your leadership regularly celebrate and communicate them?
- Do you call out and validate positive examples of good security practices? Or does your organization only focus on gaps? Do you use those examples within your security awareness program?
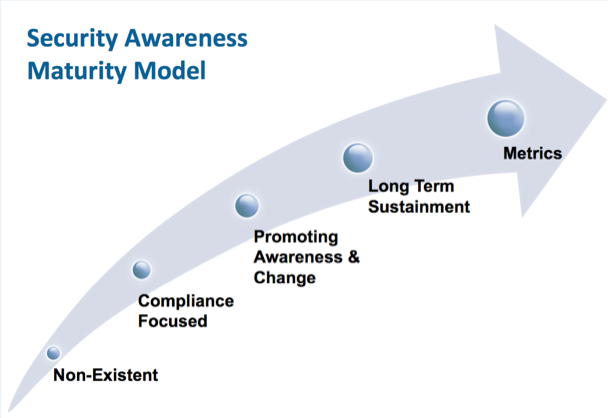
- Where do you rate your program on the security awareness maturity model shown below?
With an increasingly global and remote workforce, companies must take care to provide the appropriate level of required training. Of course all employees should be trained in your core program. However, organizations should enhance the security awareness program to include more technical training for the proper audiences. For example, executive assistants do not need to take part in training on best practices for developing secure applications. On the other hand, that training is absolutely relevant and should be be included for your application development team.
Adapting your security culture
Security awareness training is only one component of establishing a security culture in your organization. It is, however, a critical one. As existing attack vectors continue to transform and new ones are discovered, companies must continually adapt their training and validation to address the rapid rate of change in information security. For even better security, insist that vendors and partners have also established security awareness programs in their organizations. Take the time to validate the results of those programs as well. Because the world is increasingly connected, poor security awareness in a partner could create a critical impact or risk to your own organization.
We all play a role in protecting the information assets available to us. Companies must also ensure that common attack vectors are not targeting vulnerable assets. The security of your data is only as good as the weakest link in your information security playbook.



